Replication - User and group import - LDAP
Before users can be replicated from LDAP sources, the LDAP server certificate must be imported via the portal properties. So that the user can authenticate against the LDAP server, a user replication should be performed via Intrexx. A replication is not absolutely necessary for the authentication, but should be seen as the "first choice". Alternatively, users can be created manually in Intrexx with the schema (user name, domain, ...) of the LDAP server. When logging in, an attempt to authenticate against the LDAP server will be made first regardless of how the users are created.
Click here to find out where to configure an LDAP source for user and group import. Carry out the steps described there and then continue reading here.
After you have selected "LDAP" as the connection in the previous dialogs and assigned a name for it, you can now enter the connection data.
Connection parameters for the LDAP server
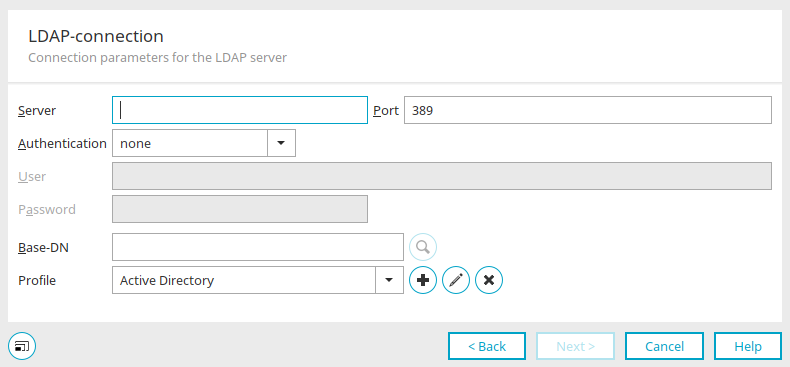
Server / Port
Enter the server name or the IP of the Active Directory server and the port. The default port for LDAP is "389" and for LDAPS "636".
Authentication
Simple authentication is usually sufficient.
Specify the user who connects to the LDAP server (e.g.: mail@example.org) and the corresponding password (login password for the domain).
Base DN
The base DN (distinguished name) is the name of the sub-tree that the users and user groups should be imported from. Select the base DN by clicking on ![]() "Search".
"Search".
Profile
Select the appropriate profile here.
![]() Create new replication profile /
Create new replication profile / ![]() Edit replication profile
Edit replication profile
Opens a dialog where a new profile can be created.
New replication profile
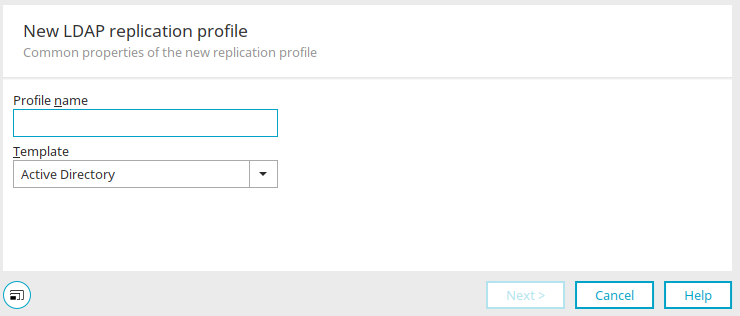
Provide the profile with a name here.
The following templates are available:
-
Active Directory
-
Active Directory Large Groups
-
Active Directory NTLM Compatible
-
Attribute Based Role Sample
-
Dynamic OU Path Sample
-
Dynamic OU Sample
-
eDirectory
-
OpenLDAP - POSIX
Click "Next".
Replication profile definition
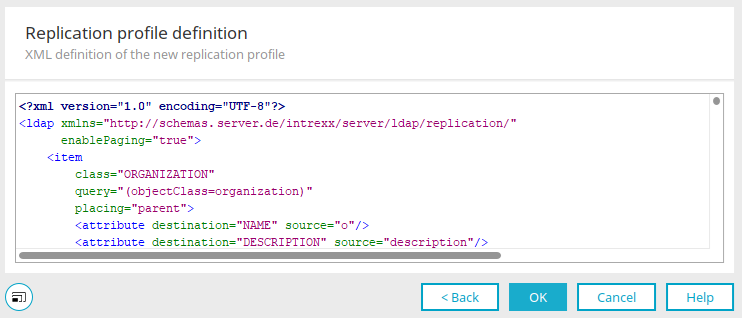
The XML of the replication profile can be edited here.
Click on "OK".

![]() Delete the replication profile
Delete the replication profile
Deletes the currently selected profile.
Click "Next".
Import settings
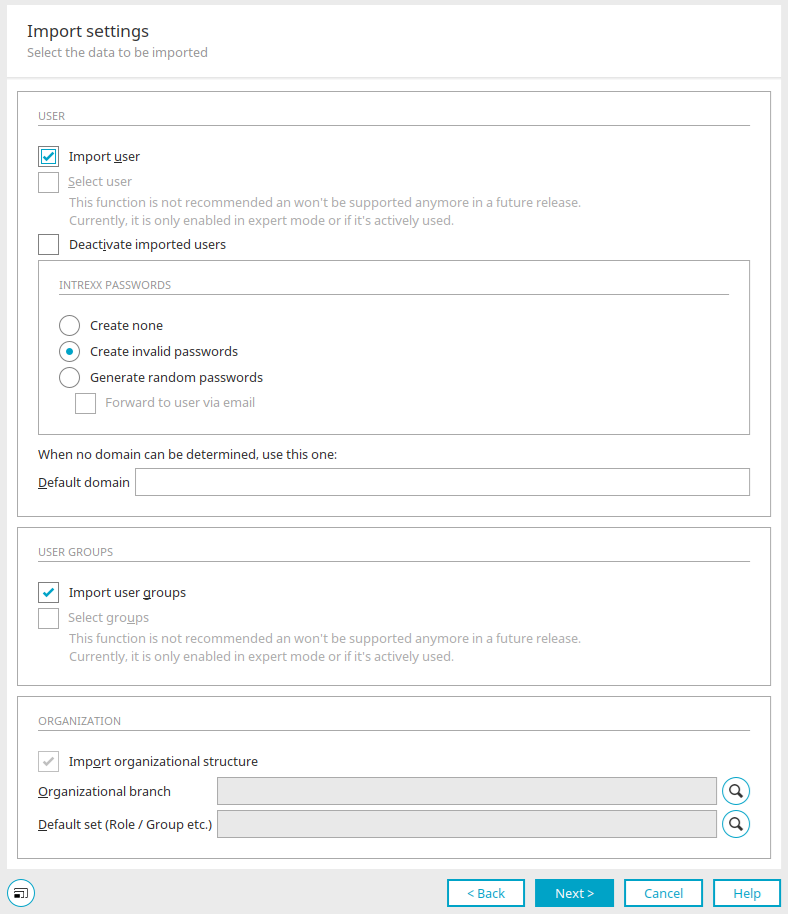
You can access this dialog for all three replication source types (LDAP, JDBC, Text). Some settings are not available for JDBC and text sources, such as the settings under "Organization".
Import user
With this setting, all users will be imported.
Search for user
This function is not recommended and will no longer be supported in the future. It is only active in expert mode or if it is already in use.
Deactivate imported users
With this setting, all user accounts of new users will first be deactivated after the import and must be activated by the administrator.
Intrexx passwords
Passwords cannot be imported, as most source systems do not provide this function for security reasons.
-
Create none
This option will cause Intrexx to not generate any passwords automatically. Users without passwords will have easy access to the portal, as only the user name is required to log in.
-
Create invalid passwords
This setting will cause Intrexx to generate pro forma unique passwords for each user. With these passwords, no login will be possible, but they can be changed by administrators in the User Manager.
-
Generate random passwords
This setting will create a password for each user after import.
-
Forward to user via email
If this setting is active, each user, which has a stored business email address, will be sent the new password automatically via email.
Default domain
If no domains can be found for an LDAP import, a standard domain can be entered here.
Import user groups
With this setting, all user groups will be imported.
Select groups
This function is not recommended and will no longer be supported in the future. It is only active in expert mode or if it is already in use.
Import organizational structure
This setting will import organizational branches.
Organizational branch
Displays the selected branch
![]() Select organizational branch
Select organizational branch
Opens a dialog where the desired user object can be selected.
Default set (Role / Group etc.)
If organizational units are imported from LDAP directories that contain no assignment of users to positions or roles, the selected position type here will be used as the default assignment.
![]() Select container
Select container
Opens a dialog where the container can be selected.
Click "Next".
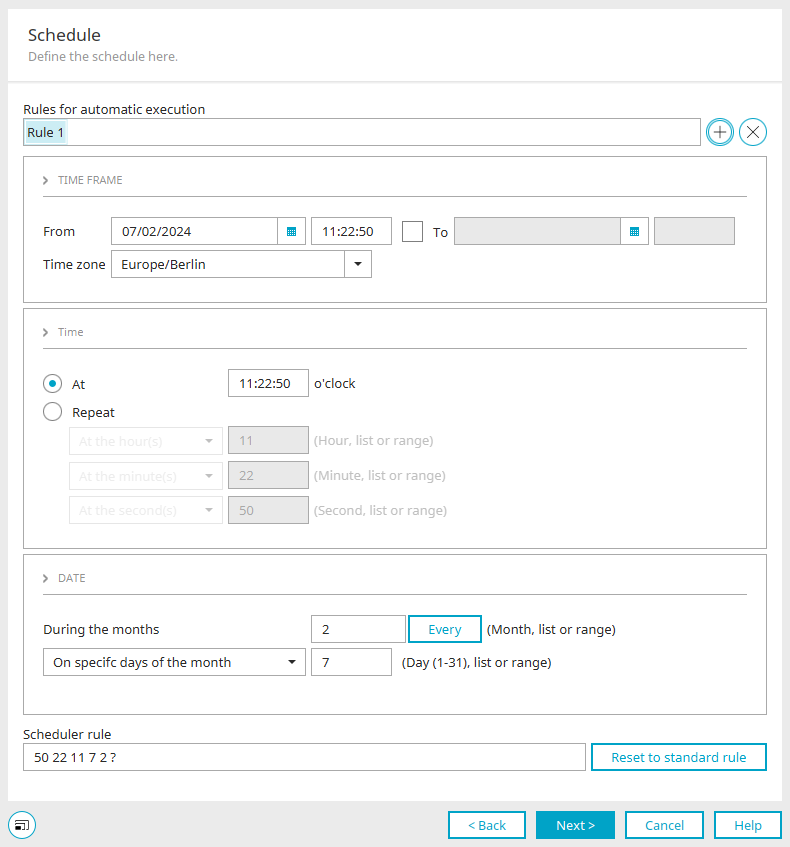
Schedule
The schedule can then be set. Detailed information on the settings for the automatic execution of replication can be found here.
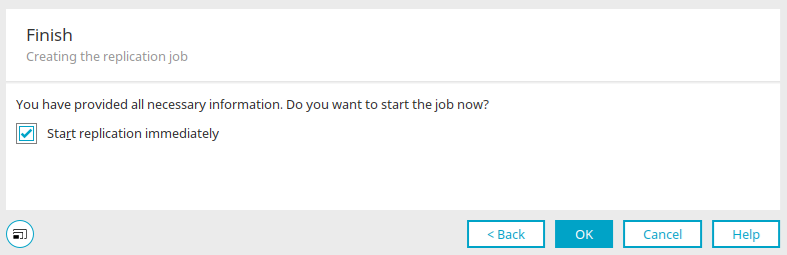
Finish
With the "Start replication" setting, the import of users is started directly after clicking on "OK".
Authentication methods
The authentication methods used by Intrexx need to be redefined.
To do this, select the main menu "Users / Configuration" in the "Users" module.
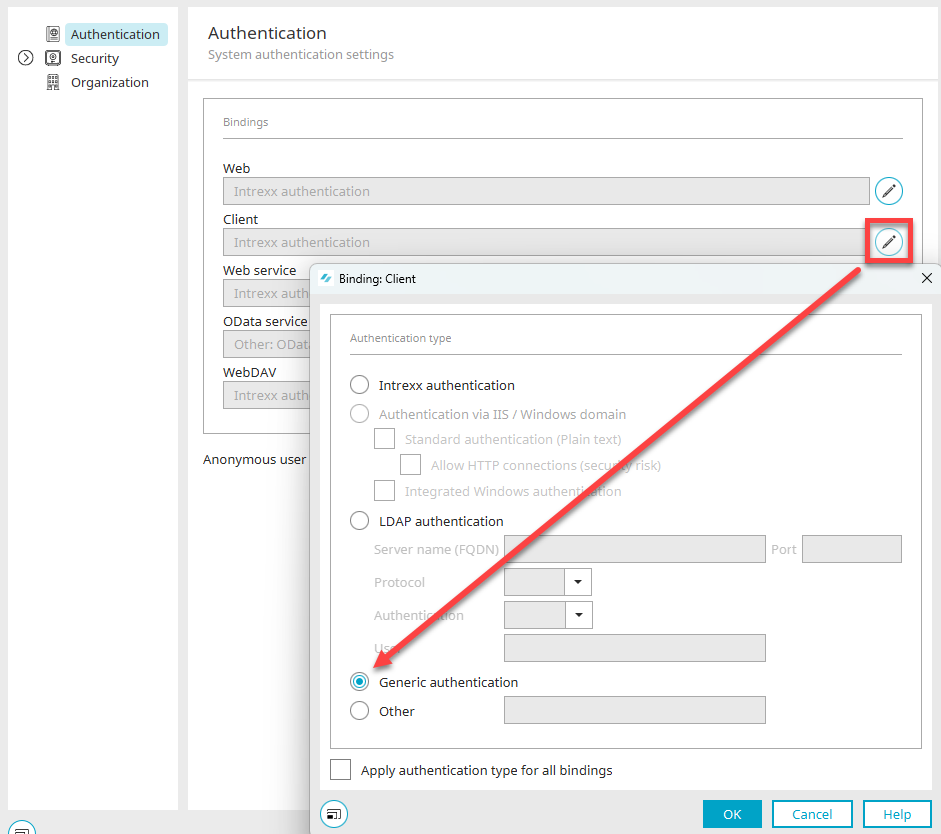
Click on ![]() "Edit binding" next to "Client". Then select the "Generic authentication" option. Close the dialog by clicking on "OK" and then log out of your portal via the main menu "Start / Disconnect portal service".
"Edit binding" next to "Client". Then select the "Generic authentication" option. Close the dialog by clicking on "OK" and then log out of your portal via the main menu "Start / Disconnect portal service".
Modify the configuration file
Open the file "LucyAuth.cfg" in the portal directory internal/cfg with a text editor of your choice. The address of the LDAP server and additional connection data need to be added to this file. Please create a backup of this file before you start editing. Please refer to the following section for more information:
GenericAuth
{
de.uplanet.lucy.server.auth.module.ldap.LdapBindLoginModule
sufficient
java.naming.provider.url="ldap://localhost:389"
java.naming.security.authentication="simple"
java.naming.security.principal="$[DN]"
debug=false;
de.uplanet.lucy.server.auth.module.anonymous.AnonymousLoginModule
sufficient
debug=false;
};
Then navigate to the following section in the text editor: How the entry needs to be modified depends on whether users were replicated from the LDAP server or created manually and then authenticate against the LDAP server. If you have performed a replication, please peform the following entries:
GenericAuth
{
de.uplanet.lucy.server.auth.module.ldap.LdapBindLoginModule
sufficient
java.naming.provider.url="ldap://ldapserver.example.org:389"
java.naming.security.authentication="simple"
java.naming.security.principal="$[DN]"
debug=false;
de.uplanet.lucy.server.auth.module.anonymous.AnonymousLoginModule
sufficient
debug=false;
};
Enter "ldap" in the provider URL if you do not use SSL encryption. Instead of "ldapserver.example.org", enter the IP address or full qualified name of the LDAP server followed by the port of the LDAP server (default: 389, SSL default: 636). The setting "$[DN]" should not be changed if the replication was successful. This distinguished name should be used for OpenLDAP, Novell eDirectory, Sun ONE and Active Directory Server. If the users were created manuall, modify the settings as follows:
GenericAuth
{
de.uplanet.lucy.server.auth.module.ldap.LdapBindLoginModule
sufficient
java.naming.provider.url="ldap://ldapserver.example.org:389"
java.naming.security.authentication="simple"
java.naming.security.principal="$[LOGIN_NAME]@$[LOGIN_DOMAIN]"
debug=false;
de.uplanet.lucy.server.auth.module.anonymous.AnonymousLoginModule
sufficient
debug=false;
};
Enter "ldap" in the provider URL if you do not use SSL encryption. Instead of "ldapserver.example.org", enter the IP address or full qualified name of the LDAP server followed by the port of the LDAP server (default: 389, SSL default: 636). $[LOGIN_NAME]@$[LOGIN_DOMAIN] is the composite principal name. Please apply this pattern exactly as it is shown above. In this way, the login only works in the Portal Manager at first. If the variant should also work when accessing the portal in the browser, the following change needs to be made to the file "initlogin.vm" in the portal directory internal/system/vm/html/login:
##Initparams for Intrexx Loginbox
##Module Subdirectory, depends on Loginmodule ## default "intrexxauth"
#set($l_strModuleSubDir = "intrexxauth")
Modify the line #set($l_strModuleSubDir = "intrexxauth") to #set($l_strModuleSubDir = "ldapauth").
Please note that login data is transferred as plain text during an LDAP authentication between the browser (client) and the server. It is there recommended to only use this method via HTTPS.