Credential store
From Intrexx version 12.0.0
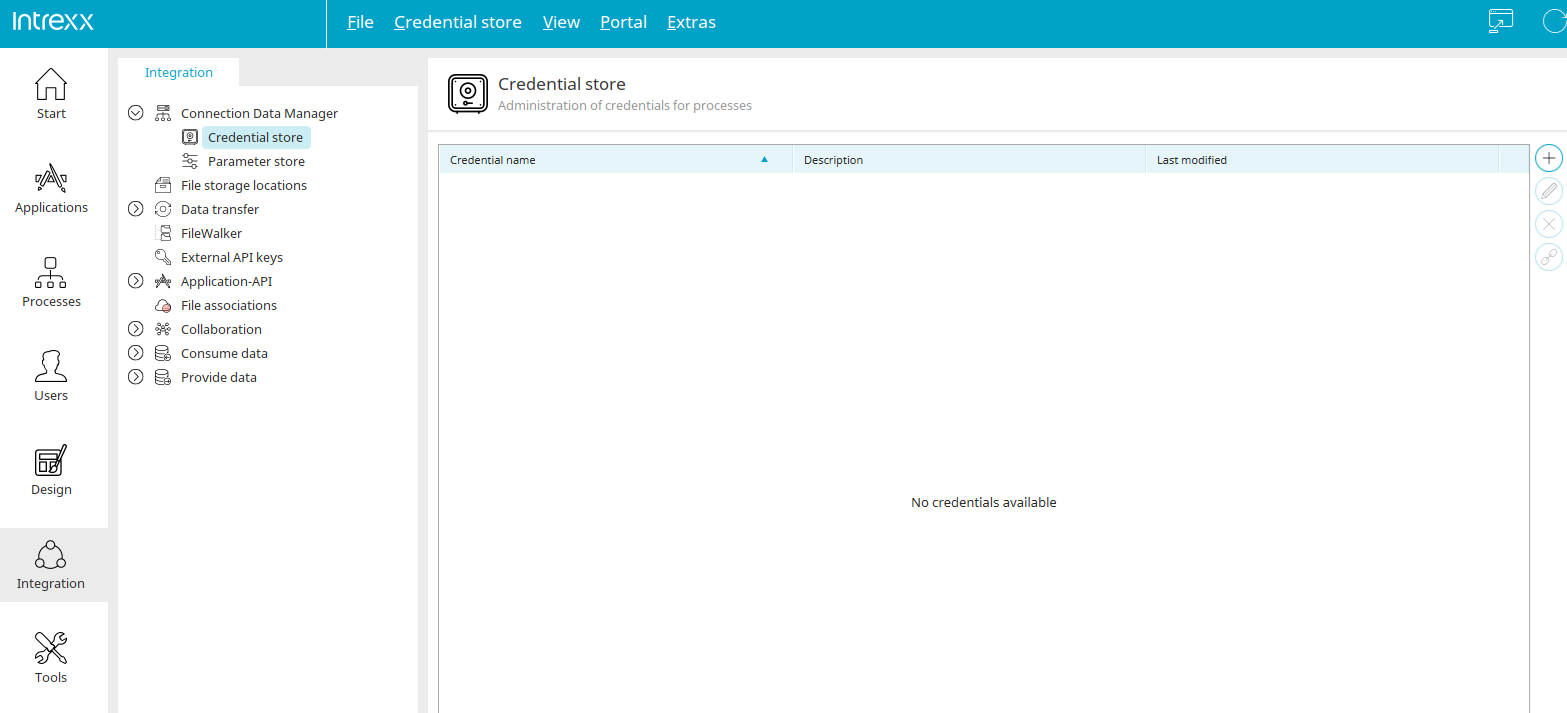
The credential store is a secure central memory area with its own namespace. You will find it in the "Integration" module on the left below the "Connection data management" item.
Credentials used in processes can be stored here independently of the processes and made available at runtime.
The Credential Store is a prerequisite for managing processes in public GIT repositories and for passing on processes to third parties. It enables an improved staging environment from the test to the live area.
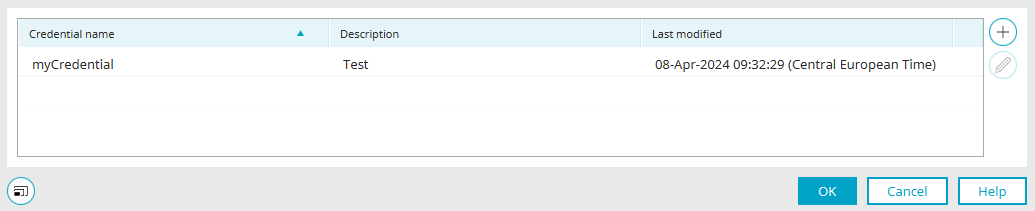
The credentials defined in the portal are listed on the right-hand side with the name, description and date of the last change.
At the top right you will find the button ![]() "Add credential". Clicking on it opens a dialog that can be used to create new credentials.
"Add credential". Clicking on it opens a dialog that can be used to create new credentials.
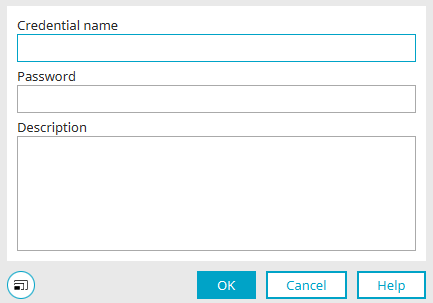
Create credential
The name of the credential must be unique and may only contain the following characters: [a-z][A-Za-z0-9]*.
Also enter the secret value of the credential here.
A description can also be entered if required.
Click "OK" to save the changes and close the dialog again.
![]() Edit login information"
Edit login information"
Opens a dialog in which the data of the credential currently selected in the list can be edited.
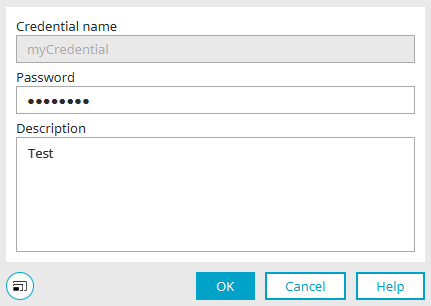
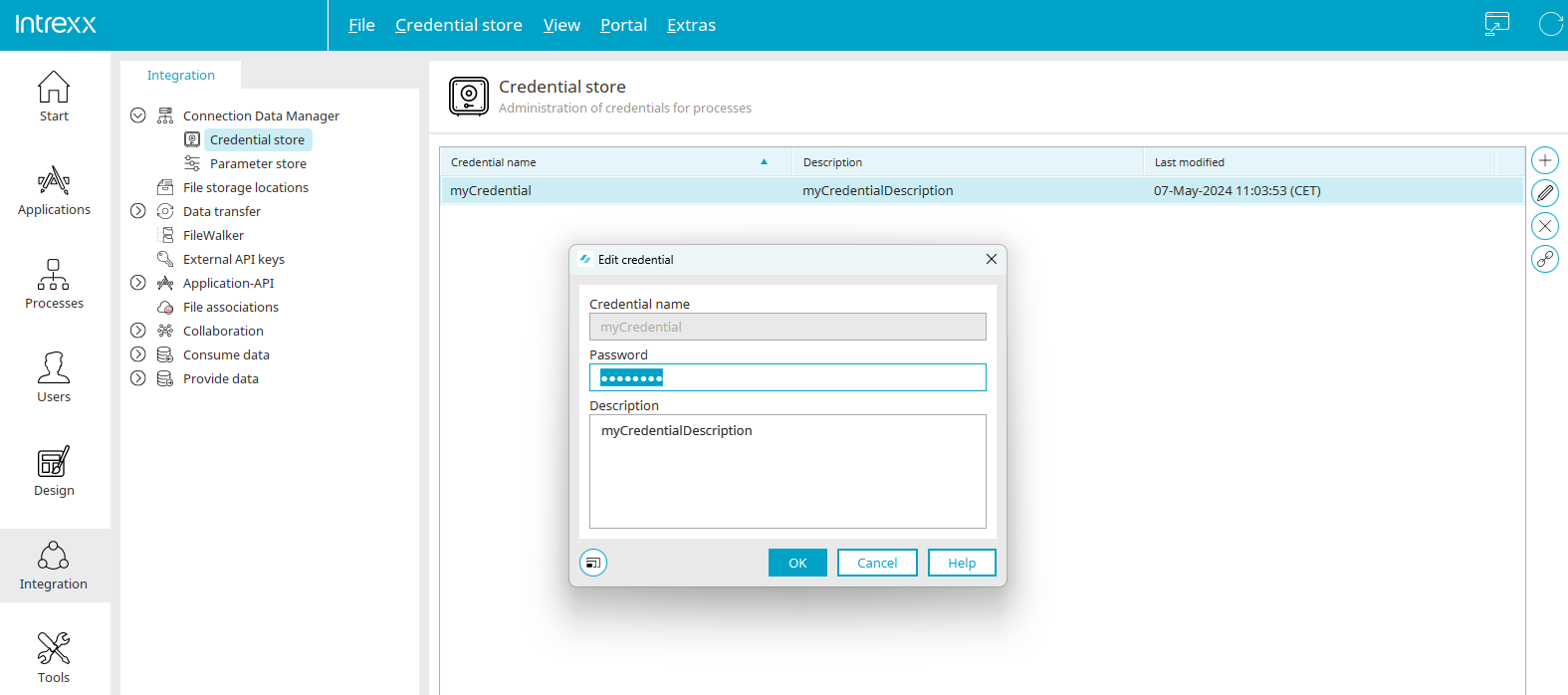
Edit credential
The name of the credential cannot be changed. The password and description can be edited. Click "OK" to save the changes and close the dialog again. The changes are applied immediately and are available at process runtime.
![]() Remove login information
Remove login information
Deletes the credential currently selected in the list. When removing, the system checks whether the selected credential is in use in processes. If yes, you will be asked whether the credential should still be deleted.
![]() Show usage in Intrexx
Show usage in Intrexx
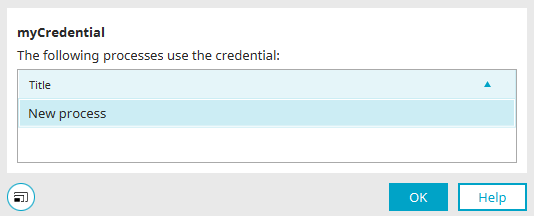
Opens a dialog in which the processes that use the credential are displayed.
Usage in Intrexx
A check is made here as to in which processes the selected credential is used. The processes found are displayed in a list.
Click "OK" to save the changes and close the dialog again.
Refresh
The credentials list can be reloaded from the server via the main menu "Credential store / Refresh" option or the corresponding ![]() button in the toolbar.
button in the toolbar.
credentialstore.cfg
All credentials are saved in the XML file "credentialstore.cfg" in the portal directory "internal/security/credentialstore". Here is an example:
<?xml version="1.0" encoding="UTF-8"?>
<credentials xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://schemas.intrexx.com/intrexx/2024/credential-store/ http://schemas.unitedplanet.de/intrexx/2024/package/de/uplanet/lucy/server/credentialstore/cfg/res/credentialstore.xsd">
<credential name="exchangeOnline" lastModified="2024-03-11T15:39:35.690Z" value="ixape-v1:58C100AF640BE086AFCCFF866ECA5405EF4325DF">
<description>Client Secret für Exchange Online</description>
</credential>
<credential name="imapServer" lastModified="2024-03-11T16:14:19.615Z" value="ixape-v1:1D9640EF237F1AFA2EADF6DF3AF253D3ED4EEAC2BD1911039E383E63FF02F8">
<description>Passwort für Standard-IMAP-Server</description>
</credential>
<credential name="imapServerTest" lastModified="2024-03-13T15:49:02.189Z" value="ixape-v1:58C100AF640BE086AFCCFF866ECA5405EF4325DF">
<description>Passwort für den Test-IMAP-Server</description>
</credential>
</credentials>
Credentials in process elements
In the "Processes" module, credentials can be selected at various points in the properties of process elements, and new credentials can also be created and added to the credential store. Alternatively, the password can also be saved directly in the process.
Credentials are stored in the BeanProperty in the form "urn:credentialStore:credentialName", where "credentialName" is the name of the credential that was assigned in the credential store.
IMAP Event Source (type "Standard IMAP")
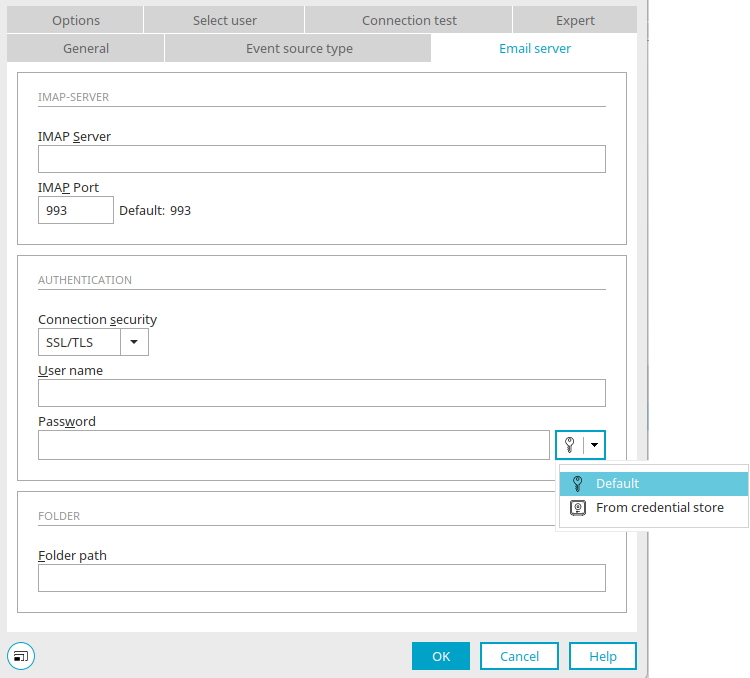
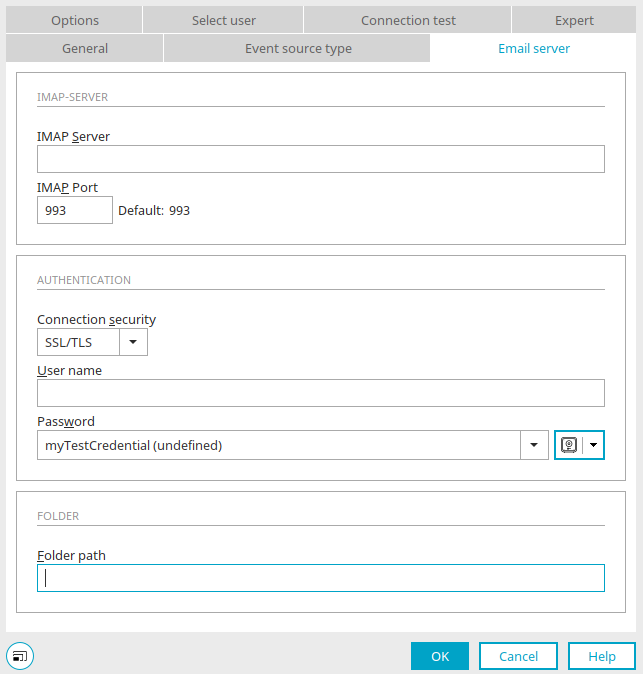
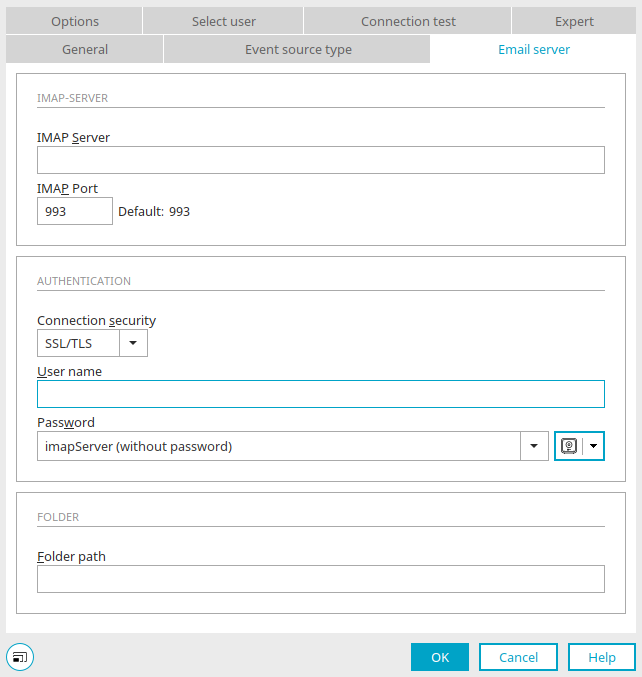
For the IMAP Event Source, the password can be set in the properties of the element on the "Email server" tab.
If you click on the small downward-pointing arrow to the right of the ![]() key symbol, a menu opens in which you can select whether the password should be saved with the process (default) or obtained from the credential store. If you select "From credential store", the
key symbol, a menu opens in which you can select whether the password should be saved with the process (default) or obtained from the credential store. If you select "From credential store", the ![]() key symbol changes and the input field for the password becomes a selection list from which you can select the desired credential. The name of the credential is then saved in the process.
key symbol changes and the input field for the password becomes a selection list from which you can select the desired credential. The name of the credential is then saved in the process.
If you click directly on the ![]() key symbol, a dialog opens in which existing credentials can be edited and new credentials can be created.
key symbol, a dialog opens in which existing credentials can be edited and new credentials can be created.
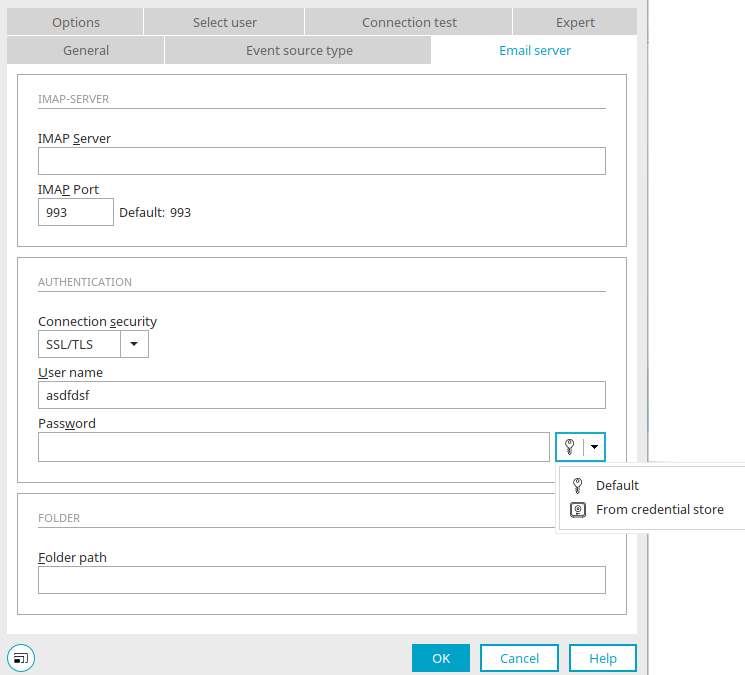
Select credential
All existing credentials are listed here. By clicking on ![]() "Add login information", new credentials can be created and existing credentials can be edited starting from here.
"Add login information", new credentials can be created and existing credentials can be edited starting from here.
IMAP Event Source (type "Exchange Online")
Here, instead of the password, the application secret (client secret) can be defined or selected in the same way as for the IMAP Event Source with the type "Standard IMAP".
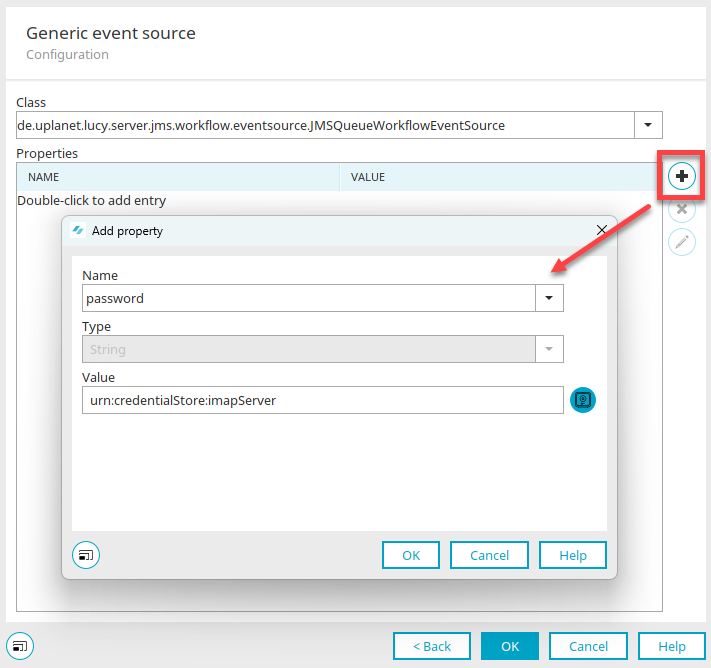
Generic elements
When editing a property, it is possible to select a credential by clicking on ![]() "Insert value from credential" if the property is of the type "String" and the annotation "@SecurityCredential" is set in the setter and getter of the bean property in the runtime class.
"Insert value from credential" if the property is of the type "String" and the annotation "@SecurityCredential" is set in the setter and getter of the bean property in the runtime class.
@SecurityCredential
public String getPassword()
{
return m_strPassword;
}
@SecurityCredential
public void setPassword(String p_strPassword)
{
m_strPassword = p_strPassword;
}
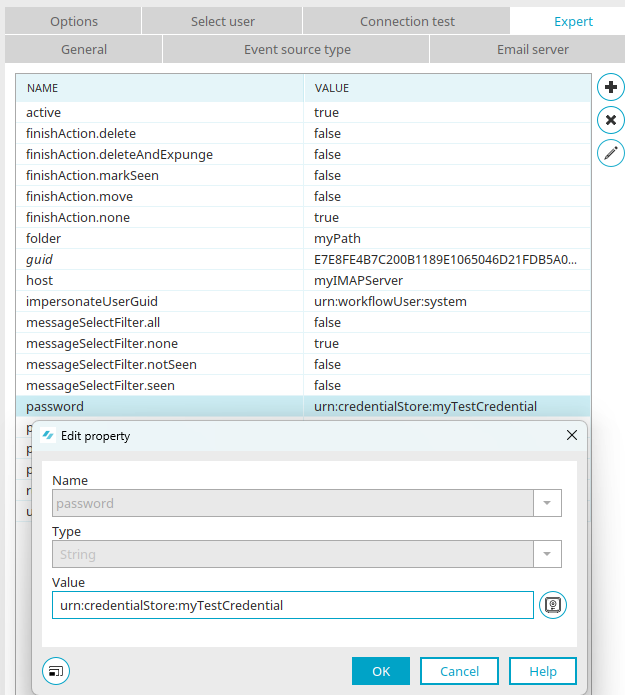
"Expert" tab
The use of credentials via the "Expert" tab in the properties of process elements works in the same way as for generic elements.
Groovy API
The context object "g_credentials" is used to access the credential store. Click here for more information.
Security
The following measures are in place to ensure the security of the Credential Store:
-
The values of the credentials are stored obfuscated in the "credentialstore.cfg".
-
Rights check: Users require the "Manage security settings" portal right to add, edit or remove credentials.
-
Restricted transport between client and server: The values of the credentials are only transported from the client to the server when they are added or edited. Conversely, no values are transported from the server to the client.
-
When exporting processes, only the names of the credentials are exported, but no values. During or after the process import, the values can be reset by the user, provided they have the required portal permission.
-
During portal export, the default setting is for the values of the credentials to be removed from credentialstore.cfg. After the portal import, the values can be reset by the user, provided they have the required portal permission.
Publication of processes
Check for undefined credentials
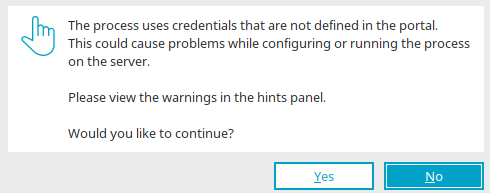
Before a process is published, the system checks whether the credentials used in the process are defined in the portal. The bean properties of the elements and the Groovy scripts are checked.
Undefined credentials can occur in a process - e.g. if an imported process contains a credential that does not exist in the current portal. If there are undefined credentials in the process, a corresponding message is displayed, which also indicates possible problems when publishing or executing the process. The user has the option of continuing or canceling the publishing process.
In the properties of the elements, undefined credentials are marked with the attribute (undefined) (exception: generic elements and "Expert" tab).
Notes tab
In addition to the notice message, the relevant elements and any Groovy script files are listed in the "Notes" area. The warning triangle shows the description of the entry when the mouse contacts it.
Double-click on an element to highlight it on the workspace.
Groovy script files can also be displayed. Double-click on the corresponding item to open the script editor. The cursor jumps to the line of the first use of an undefined credential.
metaCredential.xml
When publishing, the credential names used in the process are written to the new "metaCredential.xml" file in the process directory. The credential names are collected from the "model.xml" file and from files with the extension ".groovy".
<meta xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://schemas.intrexx.com/intrexx/2024/meta/credential/ http://schemas.unitedplanet.de/intrexx/2024/package/de/uplanet/lucy/credentialstore/meta/res/metacredential.xsd">
<credential name="imapServer"/>
<credential name="imapServerTest"/>
<credential name="myCredential"/>
</meta>
Process import
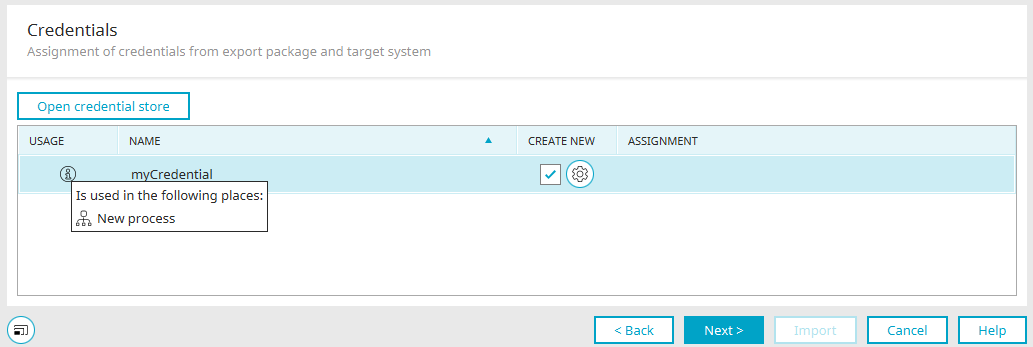
If a credential is used in at least one of the processes selected for the import, the new "Credentials" page is displayed in the import wizard.
The names of the credentials from the selected processes are displayed here. The source of the names is the respective "metaCredential.xml" file.
In the first column of the credential list, click on ![]() "Info" to display the processes in which the credential is used. The credential name is displayed in the second column.
"Info" to display the processes in which the credential is used. The credential name is displayed in the second column.
The third column contains a checkbox that can be used to create a new credential if it does not yet exist in the target portal.
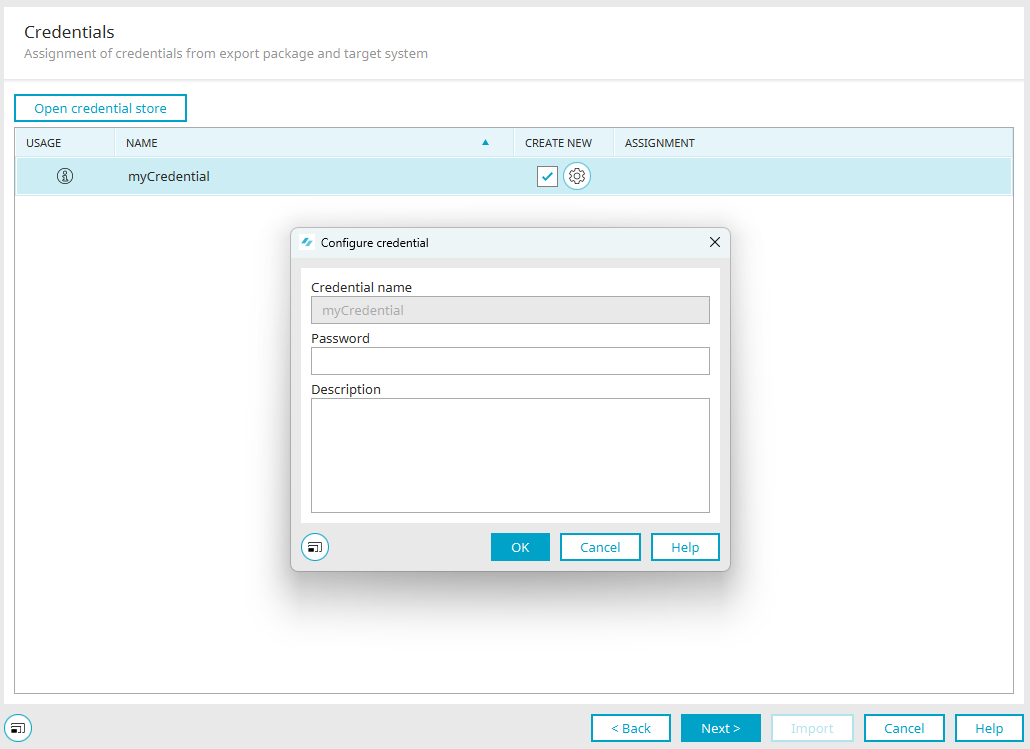
Configure credentials
Click on ![]() "Configure credentials" to open a dialog that can be used to configure the new credential. The credential must be configured when it is created, i.e. a password must be assigned. The name of the credential must be unique and may only contain the following characters: [A-Za-z][A-Za-z0-9]*. A description can also be entered optionally.
"Configure credentials" to open a dialog that can be used to configure the new credential. The credential must be configured when it is created, i.e. a password must be assigned. The name of the credential must be unique and may only contain the following characters: [A-Za-z][A-Za-z0-9]*. A description can also be entered optionally.
If the checkbox is set and the new credential is configured, it will be added to the credential store during the import process.
The "Manage security settings" portal permission is required to create new credentials.
The fourth column shows whether there is an assignment for the credential from the portal's credential store. The assignment takes place automatically if a credential with the same name as in the import package exists in the portal. An assignment with a different name is not possible, since the use in Groovy scripts cannot be determined 100% reliably and therefore an adaptation of the name would not be possible in every case.
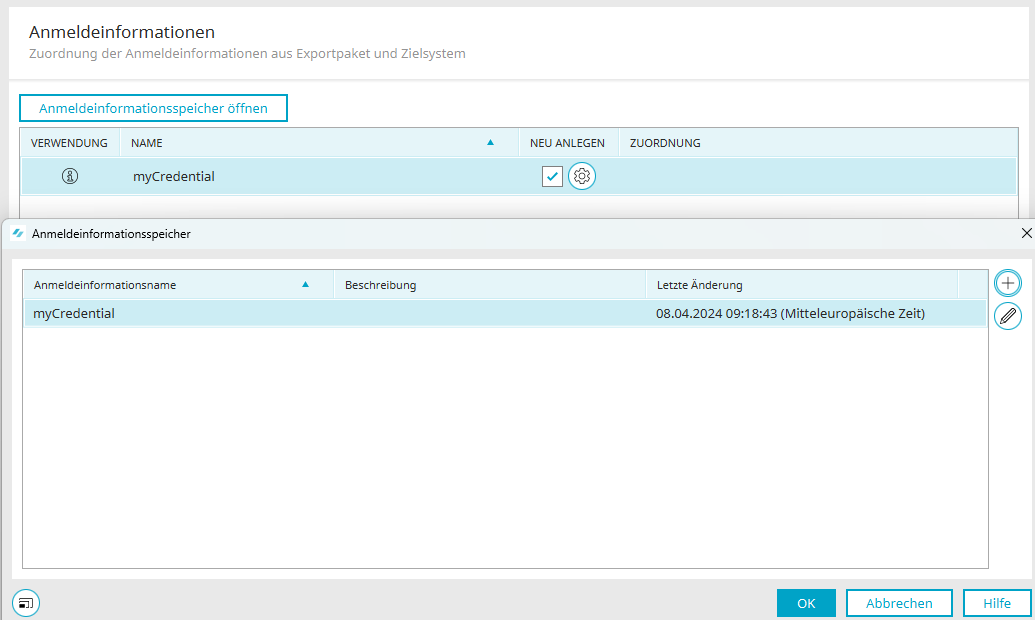
Alternatively, missing credentials can also be added immediately to the portal's credential store. To do this, open the credential store using the "Open credential store" button. Click here for more information.
The assignments to the portal are updated when the dialog is closed.
If not all credentials are assigned or the creation of new credentials is not fully configured, a message is displayed when you click on "Next". The import can still be continued on request.
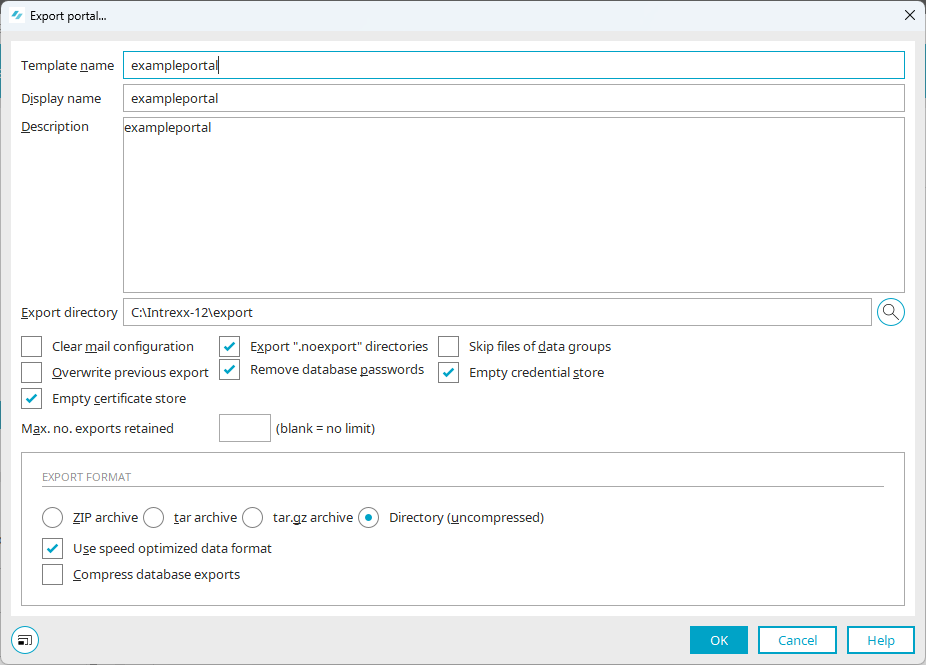
Portal export
With the setting "Clear credential store", the values (passwords) of the credentials in the file "internal/security/credentialstore/credentialstore.cfg" are removed in the portal export and are therefore not transferred. Existing credentials are then exported with the name and description only. This has the advantage that the credentials with the name and description are still available in the credential store after the portal import and the processes in which they are used can also be displayed for each credential.
Here is the "credentialstore.cfg" file after the portal export with the option enabled:
<?xml version="1.0" encoding="UTF-8"?>
<credentials xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://schemas.intrexx.com/intrexx/2024/credential-store/ http://schemas.unitedplanet.de/intrexx/2024/package/de/uplanet/lucy/server/credentialstore/cfg/res/credentialstore.xsd">
<credential name="exchangeOnline" lastModified="2024-03-11T15:39:35.690Z">
<description>Client Secret für Exchange Online</description>
</credential>
<credential name="imapServer" lastModified="2024-03-11T16:14:19.615Z">
<description>Passwort für Standard-IMAP-Server</description>
</credential>
<credential name="imapServerTest" lastModified="2024-03-13T15:49:02.189Z">
<description>Passwort für den Test-IMAP-Server</description>
</credential>
</credentials>
The names and descriptions of the credentials are retained so that only the values need to be reset after the portal import and there is no need to create all the credentials again. This also retains the reference to the processes so that, for example, you can display the use of the credential in the credential store. The default setting is "Clear credential store".
General information on the subject of "Portal export" can be found here.
Portal export via script
-
Linux: $INTREXX_HOME/bin/linux/exportportal.sh
-
MaxosX: $INTREXX_HOME/bin/macosx/exportportal.sh
-
Windows: %INTREXX_HOME%/bin/windows/exportportal.bat
USAGE:
portalexport [options]
Options:
--destination=<destination> destination directory,
Default is <IntrexxDir>/export.
--format=<format> output format. Possible values are
zip, tar, tgz and plain.
Default format is zip.
--ignoreNoExport Ignore the .noexport flag in folders
--cleanMailConfig Clear mail configuration
--exportPassword Database passwords will be exported.
On default no database passwords will be exported.
--exportCredentialStore Exports the credentials store with passwords.
On default the credential store will export
without passwords.
--exportTrustStore The certificate store will be exported.
On default the original credential store from the
blank portal will be exported.
--skipFiles Skip files of data groups
--optimize Use speed optimized data format
--compress Compress database exports
--verbose Verbose mode
--silent Silent mode
Portal import
During portal import, the "credentialstore.cfg" file is transferred to the portal in the same way as in the portal export. If values are missing, a warning triangle is displayed for the respective credential in the credential store. The missing value is also indicated in the edit dialog. The password can be reset there.
In the properties of elements, credentials without a value are marked with the attribute "(no password)" - with the exception of generic elements and on the "Expert" tab.