More information In some scenarios, it is necessary to use a personalized SAP access. At least the system user stored in the SAP data source is used for access to SAP. However, it is also possible to use a user-dependent SAP user to then observe the permissions defined in the SAP system or avoid logging in to SAP again. This section will explain how requirements such as
-
Password check by SAP
-
Access to SAP with the real SAP user
-
Calling SAP websites (WebDynpro, BSP applications) with Single Sign On (SSO)
-
Starting SAPGUI transactions with the transfer of parameters
can be implemented.
Login mode
The login mode plays a role in many places with SAP access. The following login modes are used by the Connector for SAP Business Suite:
|
Login mode |
Use |
|---|---|
|
system |
Use the system user defined in the SAP data source |
|
user |
Exclusive use of the personal login information of the logged-in portal user. This information is determined without login information being determined. If these are incorrect, access to SAP is not possible. |
|
mixed |
Intrexx attempts to make access in the user mode. If this fails, the system mode is used. |
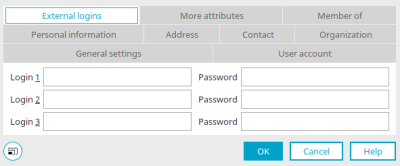
The login information for each portal user can be stored in the Intrexx user administration as an external login.
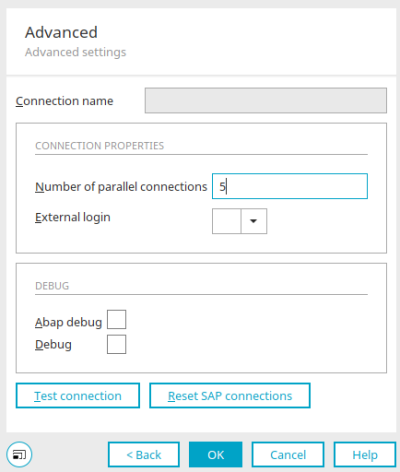
The external login used to log in to the SAP system can be specified in the SAP data source.
Alternatively, a portal login with password check is possible against an SAP system. Here, the password entered is checked against the specified SAP system. Intrexx needs to have an identically named user base for this. Parallel password maintenance / replication is not necessary in this case. This login type also enables single sign-on scenarios via SAP logon tickets. Via the script API of the Connector for SAP Business Suite, you can deliberately influence the personalized access to enable further login scenarios in projects.
SAP login modules
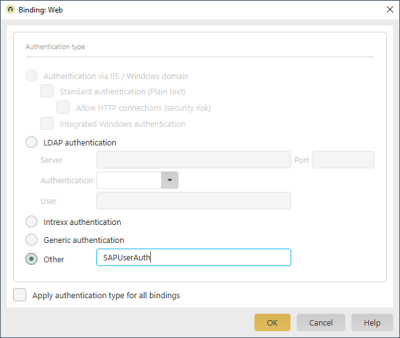
Intrexx login modules enable authorization to the portal from external positions. The check against an external LDAP server is included in the standard login modules, for example. The portal login can be configured to run different login modules one after the other until one of the login modules has authorized the portal user. A user master must exist in Intrexx for each possible portal user, but this does not have to contain a password check and can be replicated via Intrexx on-board tools.the connector for SAP Business Suite comes with its own login modules, which, for example, implement the password checks by SAP for SAP users, SU05 Internet users or SAP business partners. The portal login and the login modules to be called up are maintained in the "LucyAuth.cfg" configuration file of the portal. A login configuration that first checks the SAP user master, then the SU05 Internet users of the customer master and then the Intrexx standard login is shown here:
SapUserAuth
{
net.initall.ixapi.auth.IxSAPLoginModuleUser sufficient
instance="saperp"
mapuser=false
initjco=false
debug=false;
net.initall.ixapi.auth.IxSAPLoginModuleIUser sufficient
instance="saperp"
logintype="KNA1"
initjco=false
debug=false;
de.uplanet.lucy.server.auth.module.intrexx.IntrexxLoginModule sufficient
debug=false;
de.uplanet.lucy.server.auth.module.anonymous.AnonymousLoginModule sufficient
debug=false;
};
This configuration is then activated via the Portal Manager in the user administration via the main menu Users / Configuration / Authentication.
The SAP login module used here is the prerequisite for generating SAP login tickets that are used in single sign-on scenarios. When the portal user successfully logs in to the SAP system, such a ticket is automatically generated, which can then be used later to integrate SAP internet pages or SAP shortcuts.
Single Sign On with SAP logon tickets
Single Sign On (SSO) or avoiding unnecessary multiple logins is achieved with Intrexx via SAP logon tickets. Information on this can be found in SAP note "304450", for example. The SAP server must issue and accept SSO tickets (RZ10 parameters "login/accept*" and "login/create*"). The "TRUSTSSO2" transaction must also be initialized. The portal creates a ticket via the SAP function module "SUSR_CHECK_LOGON_DATA" in the specified SAP system, which is later available for SSO scenarios. This procedure is provided by the SAP login modules. The SAP system must be configured for the use of logon tickets (see SAP Note "612670"). Currently, only authorization with SAP user name or alias and password is supported (function module "SUSR_CHECK_LOGON_DATA: AUTH_METHOD = "P""). Further tests may be made available at a later date or can be implemented in projects.
More information
SAP Trust Manager SSO configuration
API Description Part 1 - Overview
API Description Part 2 - SAP Portal Plugin
API description part 3 - Implementation of own processing modules
API description part 4 - sample coding
Developer's Guide Part 2 - Integration scenario SAP external data group
Developer's Guide Part 3 - Scripting integration scenario