Im Folgenden finden Sie eine Beschreibung, wie NGINX als Reverse-Proxy für Intrexx konfiguriert wird.
Wenn sie eigene Konfigurationen für Web-Frontends (Nginx, IIS, Apache, HAProxy, TrafficServer o.ä.) erstellen möchten, beachten Sie Folgendes:
HTTPS
-
Zugriff nur per HTTPS
-
Redirect von HTTP auf HTTPS
Blockierte URLs
-
Versteckte Dateien und Verzeichnisse beginnend mit .. Ausnahme : /.well-known/
-
/WEB-INF/ (rekursiv)
-
/web.config
-
/bin/ (rekursiv)
1. Konfigurationsdatei anpassen
Ersetzen Sie bei einem Upgrade in der NGINX-Konfigurationsdatei die Zeile
location ~ (css|download|images|include|is|script|temp|thirdparty|userfiles) {
durch die folgende Zeile
location ~ ^(/css|/fonts|/images|/include|/script|/thirdparty|/userfiles|/download|/is) {
In der Regel sind Nginx-Konfigurationsdateien betroffen, die mit Intrexx 20.09, 20.03 OU3, 19.09, 19.03 OU13 oder älter erstellt wurden.
Intrexx Version 12.0.1
Die Anpassungen für Intrexx 12.0.1 stehen im Zusammenhang mit den geänderten Zugriffsmöglichkeiten für das Verzeichnis "userfiles" ("<portal-verzeichnis> \external\htmlroot\userfiles"), in das bei entsprechender Konfiguration Bilddateien von Portalbenutzern hochgeladen und von dort auch wieder heruntergeladen werden können.
Weitere Informationen hierzu finden Sie in Abschnitt Portaleigenschaften - Sicherheit - Upload/Download.
Bis Intrexx 12.0.0 wurden die Bilddateien über den Fronten Webserver (Reverse Proxy) zur Verfügung gestellt. Ab Intrexx 12.0.1 geschieht dies über den in Intrexx integrierten Webserver (Tomcat). Aus diesem Grund muss das Verzeichnis "userfiles" aus der Konfigurationsdatei entfernt werden.
Weitere Informationen zum Fronten Webserver (Reverse Proxy) und zum Embedded Tomcat finden Sie in Abschnitt Frontend Webserver (Reverse Proxy) verwenden.
Ersetzen Sie bei einem Upgrade in der NGINX-Konfigurationsdatei die Zeile
location ~ (css|download|images|include|is|script|temp|thirdparty|userfiles) {
durch die folgende Zeile
location ~ ^(/css|/fonts|/images|/include|/script|/thirdparty) {
In der Regel sind Nginx-Konfigurationsdateien betroffen, die mit Intrexx 20.09, 20.03 OU3, 19.09, 19.03 OU13 oder älter erstellt wurden.
Die Konfiguration von NGINX erfolgt über Konfigurationsdateien. Nachdem Sie die Intrexx-Setup-Dateien heruntergeladen haben, finden Sie drei Vorlagendateien für das Konfigurieren von NGINX. Diese können Sie als Basis für die Konfiguration Ihres NGINX verwenden.
Die Vorlagendateien finden Sie unter folgendem Pfad: <INTREXX-ROOT>/samples/web-tls-configuration/nginx/
Die Namen der Vorlagendateien lauten portal-intranet.conf, portal-internet.conf und portal-remote.conf
Hinweis Die Datei "portal-internet.conf" enthält über die Angaben in der Datei "portal-intranet.conf" hinaus noch zusätzlich einen Abschnitt für die Konfiguration des OCSP-Staplings.
Über die folgenden aufklappbaren Links können Sie sich die Dateien ansehen und sich so bereits einen Überblick verschaffen.
#
# This file may be used as a basic template for running Intrexx behind Nginx.
#
# Nginx performs the required TLS encryption and serves certain static files.
#
# TODO tags indicate which directives have to be modified in your configuration.
#
# Define the upstream connections.
#
# TODO: Ensure that the upstream name (here "backend") is
# unique for all virtual servers that run under this Nginx
# instance.
#
upstream backend {
# Address and port of the Intrexx Portal Service
#
# TODO: Configure the actual address and port of your Intrexx
# Portal Service web connector.
#
server localhost:1337;
}
# Redirect all unencrypted HTTP requests to HTTPS.
#
# TODO: Change the server name and redirect URL.
#
server {
listen 80;
server_name intrexx.example.org;
rewrite ^ https://intrexx.example.org$request_uri? permanent;
rewrite_log on;
}
# Reverse proxy with TLS offloading for the Intrexx Portal Service.
#
server {
listen 443 ssl;
server_name intrexx.example.org;
keepalive_timeout 70s;
# Use dedicated access and error logs.
#
# TODO: If you want to have dedicated access and error logs for
# your Intrexx portal then uncomment the directives below and
# change the paths to fit your needs.
#
#access_log /var/log/nginx/intrexx.example.org-access.log;
#error_log /var/log/nginx/intrexx.example.org-error.log error;
# SSL keys, certificates and optional DHE group
#
# Note: Here the term "modern compatibility" refers to configurations
# that support TLSv1.3 only, while intermediate compatibility supports
# both TLSv1.3 and TLSv1.2.
# See https://wiki.mozilla.org/Security/Server_Side_TLS for additional
# information about which one to choose according to your requirements.
#
# TODO: Configure the actual paths to your certificate and key files.
# For intermediate compatibility copy the provided Diffie-Hellman
# parameters file to an appropriate location specified with the
# ssl_dhparam directive.
# See https://wiki.mozilla.org/Security/Server_Side_TLS#Forward_Secrecy.
#
# The file specified by ssl_certificate should contain the certificate
# chain starting with your server certificate, following the intermediate
# certificates, up to the root certificate. The root certificate may be
# left out for SSL handshake optimization.
#
# The file specified by ssl_trusted_certificate should contain the certificate
# chain starting with your server certificate, following the intermediate
# certificates, up to the root certificate.
#
# As the Diffie-Hellman parameters file you might want to use one of the
# ffdhe*.pem files from samples/web-tls-configuration/nginx/.
#
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_certificate
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_trusted_certificate (for OCSP)
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_password_file
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_dhparam
# https://tools.ietf.org/html/rfc7919
#
ssl_certificate /etc/ssl/localcerts/intrexx.example.org.pem;
ssl_trusted_certificate /etc/ssl/localcerts/intrexx.example.org.pem;
ssl_certificate_key /etc/ssl/localcerts/intrexx.example.org.key;
#ssl_password_file /etc/ssl/localcerts/intrexx.example.org.password;
ssl_dhparam /etc/ssl/localcerts/ffdhe2048.pem;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 30m;
ssl_session_tickets on;
# Configure the TLS protocols
#
# TODO: Choose one of modern or intermediate compatibility below.
#
# Modern compatibility (TLSv1.3 only)
#
# TODO: For modern compatibility uncomment the line below.
#
#ssl_protocols TLSv1.3;
# Intermediate compatibility
#
# TODO: For modern compatibility comment out the three lines below.
#
ssl_protocols TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers 'TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384';
add_header Strict-Transport-Security max-age=63072000; # two years
add_header X-Frame-Options SAMEORIGIN;
# The root path of the Intrexx web application.
#
# TODO: Specify the path to your portal's htmlroot directory.
#
root /opt/intrexx/org/intrexx.example.org/external/htmlroot;
# serve favicon and robots.txt
location ~ (/favicon.ico|/robots.txt) {
try_files $uri =404;
}
# hide hidden files and directories
location ~ /\. {
return 404;
}
# hide WEB-INF
location /WEB-INF/ {
deny all;
return 404;
}
# hide IIS web.config
location ~* /web.config {
deny all;
return 404;
}
# hide the bin directory
location /bin/ {
deny all;
return 404;
}
# Static files that should be served by Nginx.
#
location ~ ^(/css|/fonts|/images|/include|/script|/thirdparty) {
sendfile on;
sendfile_max_chunk 1m;
try_files $uri =404;
}
# Delegate WebSocket requests to the Intrexx Portal Service.
#
location /ws/ {
proxy_pass http://backend;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "Upgrade";
}
# Delegate requests to the Intrexx Portal Service.
#
location / {
proxy_pass http://backend;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
# Clear potentially unsafe headers. These may be enabled if the backend
# is configured to handle them correctly and in a safe manner.
proxy_set_header Forwarded "";
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Host $host:$server_port;
proxy_set_header X-Original-URL "";
# Security token to authenticate the reverse proxy with the backend.
proxy_set_header X-SecToken "";
# For security reasons we do not pass X-User and X-Domain to the backend by default,
# since these headers might be interpreted by the External Authentication Filter as
# authenticated user information.
proxy_set_header X-User "";
proxy_set_header X-Domain "";
# additional security sensitive headers
proxy_set_header X-KrbTicket "";
proxy_set_header X-AccountName "";
# Set the maximum allowed size of the client request body. The value 0 disables
# this limit check.
# http://nginx.org/en/docs/http/ngx_http_core_module.html#client_max_body_size
client_max_body_size 2048m;
}
}#
# This file may be used as a basic template for running Intrexx behind Nginx.
#
# Nginx performs the required TLS encryption and serves certain static files.
#
# TODO tags indicate which directives have to be modified in your configuration.
#
# Define the upstream connections.
#
# TODO: Ensure that the upstream name (here "backend") is
# unique for all virtual servers that run under this Nginx
# instance.
#
upstream backend {
# Address and port of the Intrexx Portal Service
#
# TODO: Configure the actual address and port of your Intrexx
# Portal Service web connector.
#
server localhost:1337;
}
# Redirect all unencrypted HTTP requests to HTTPS.
#
# TODO: Change the server name and redirect URL.
#
server {
listen 80;
server_name intrexx.example.org;
rewrite ^ https://intrexx.example.org$request_uri? permanent;
rewrite_log on;
}
# Reverse proxy with TLS offloading for the Intrexx Portal Service.
#
server {
listen 443 ssl;
server_name intrexx.example.org;
keepalive_timeout 70s;
# Use dedicated access and error logs.
#
# TODO: If you want to have dedicated access and error logs for
# your Intrexx portal then uncomment the directives below and
# change the paths to fit your needs.
#
#access_log /var/log/nginx/intrexx.example.org-access.log;
#error_log /var/log/nginx/intrexx.example.org-error.log error;
# SSL keys, certificates and optional DHE group
#
# Note: Here the term "modern compatibility" refers to configurations
# that support TLSv1.3 only, while intermediate compatibility supports
# both TLSv1.3 and TLSv1.2.
# See https://wiki.mozilla.org/Security/Server_Side_TLS for additional
# information about which one to choose according to your requirements.
#
# TODO: Configure the actual paths to your certificate and key files.
# For intermediate compatibility copy the provided Diffie-Hellman
# parameters file to an appropriate location specified with the
# ssl_dhparam directive.
# See https://wiki.mozilla.org/Security/Server_Side_TLS#Forward_Secrecy.
#
# The file specified by ssl_certificate should contain the certificate
# chain starting with your server certificate, following the intermediate
# certificates, up to the root certificate. The root certificate may be
# left out for SSL handshake optimization.
#
# The file specified by ssl_trusted_certificate should contain the certificate
# chain starting with your server certificate, following the intermediate
# certificates, up to the root certificate.
#
# As the Diffie-Hellman parameters file you might want to use one of the
# ffdhe*.pem files from samples/web-tls-configuration/nginx/.
#
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_certificate
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_trusted_certificate (for OCSP)
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_password_file
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_dhparam
# https://tools.ietf.org/html/rfc7919
#
ssl_certificate /etc/ssl/localcerts/intrexx.example.org.pem;
ssl_trusted_certificate /etc/ssl/localcerts/intrexx.example.org.pem;
ssl_certificate_key /etc/ssl/localcerts/intrexx.example.org.key;
#ssl_password_file /etc/ssl/localcerts/intrexx.example.org.password;
ssl_dhparam /etc/ssl/localcerts/ffdhe2048.pem;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 30m;
ssl_session_tickets on;
# Enable or disable OCSP Stapling
#
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_stapling
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_stapling_verify
# http://nginx.org/en/docs/http/ngx_http_core_module.html#resolver
#
ssl_stapling on;
ssl_stapling_verify on;
resolver 9.9.9.9 8.8.8.8 valid=300s;
# Configure the TLS protocols
#
# TODO: Choose one of modern or intermediate compatibility below.
#
# Modern compatibility (TLSv1.3 only)
#
# TODO: For modern compatibility uncomment the line below.
#
#ssl_protocols TLSv1.3;
# Intermediate compatibility
#
# TODO: For modern compatibility comment out the three lines below.
#
ssl_protocols TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers 'TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384';
add_header Strict-Transport-Security max-age=63072000; # two years
add_header X-Frame-Options SAMEORIGIN;
# The root path of the Intrexx web application.
#
# TODO: Specify the path to your portal's htmlroot directory.
#
root /opt/intrexx/org/intrexx.example.org/external/htmlroot;
# serve favicon and robots.txt
location ~ (/favicon.ico|/robots.txt) {
try_files $uri =404;
}
# hide hidden files and directories
location ~ /\. {
return 404;
}
# hide WEB-INF
location /WEB-INF/ {
deny all;
return 404;
}
# hide IIS web.config
location ~* /web.config {
deny all;
return 404;
}
# hide the bin directory
location /bin/ {
deny all;
return 404;
}
# Static files that should be served by Nginx.
#
location ~ ^(/css|/fonts|/images|/include|/script|/thirdparty) {
sendfile on;
sendfile_max_chunk 1m;
try_files $uri =404;
}
# Delegate WebSocket requests to the Intrexx Portal Service.
#
location /ws/ {
proxy_pass http://backend;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "Upgrade";
}
# Delegate requests to the Intrexx Portal Service.
#
location / {
proxy_pass http://backend;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
# Clear potentially unsafe headers. These may be enabled if the backend
# is configured to handle them correctly and in a safe manner.
proxy_set_header Forwarded "";
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Host $host:$server_port;
proxy_set_header X-Original-URL "";
# Security token to authenticate the reverse proxy with the backend.
proxy_set_header X-SecToken "";
# For security reasons we do not pass X-User and X-Domain to the backend by default,
# since these headers might be interpreted by the External Authentication Filter as
# authenticated user information.
proxy_set_header X-User "";
proxy_set_header X-Domain "";
# additional security sensitive headers
proxy_set_header X-KrbTicket "";
proxy_set_header X-AccountName "";
# Set the maximum allowed size of the client request body. The value 0 disables
# this limit check.
# http://nginx.org/en/docs/http/ngx_http_core_module.html#client_max_body_size
client_max_body_size 2048m;
}
}#
# This file may be used as a basic template for running Intrexx behind Nginx
# when Intrexx and Nginx reside on different machines.
#
# Nginx performs the required TLS encryption.
#
# TODO tags indicate which directives have to be modified in your configuration.
#
# Define the upstream connections.
#
# TODO: Ensure that the upstream name (here "backend") is
# unique for all virtual servers that run under this Nginx
# instance.
#
upstream backend {
# Address and port of the Intrexx Portal Service
#
# TODO: Configure the actual address and port of your Intrexx
# Portal Service web connector.
#
server localhost:1337;
}
# Redirect all unencrypted HTTP requests to HTTPS.
#
# TODO: Change the server name and redirect URL.
#
server {
listen 80;
server_name intrexx.example.org;
rewrite ^ https://intrexx.example.org$request_uri? permanent;
rewrite_log on;
}
# Reverse proxy with TLS offloading for the Intrexx Portal Service.
#
server {
listen 443 ssl;
server_name intrexx.example.org;
keepalive_timeout 70s;
# Use dedicated access and error logs.
#
# TODO: If you want to have dedicated access and error logs for
# your Intrexx portal then uncomment the directives below and
# change the paths to fit your needs.
#
#access_log /var/log/nginx/intrexx.example.org-access.log;
#error_log /var/log/nginx/intrexx.example.org-error.log error;
# SSL keys, certificates and optional DHE group
#
# Note: Here the term "modern compatibility" refers to configurations
# that support TLSv1.3 only, while intermediate compatibility supports
# both TLSv1.3 and TLSv1.2.
# See https://wiki.mozilla.org/Security/Server_Side_TLS for additional
# information about which one to choose according to your requirements.
#
# TODO: Configure the actual paths to your certificate and key files.
# For intermediate compatibility copy the provided Diffie-Hellman
# parameters file to an appropriate location specified with the
# ssl_dhparam directive.
# See https://wiki.mozilla.org/Security/Server_Side_TLS#Forward_Secrecy.
#
# The file specified by ssl_certificate should contain the certificate
# chain starting with your server certificate, following the intermediate
# certificates, up to the root certificate. The root certificate may be
# left out for SSL handshake optimization.
#
# The file specified by ssl_trusted_certificate should contain the certificate
# chain starting with your server certificate, following the intermediate
# certificates, up to the root certificate.
#
# As the Diffie-Hellman parameters file you might want to use one of the
# ffdhe*.pem files from samples/web-tls-configuration/nginx/.
#
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_certificate
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_trusted_certificate (for OCSP)
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_password_file
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_dhparam
# https://tools.ietf.org/html/rfc7919
#
ssl_certificate /etc/ssl/localcerts/intrexx.example.org.pem;
ssl_trusted_certificate /etc/ssl/localcerts/intrexx.example.org.pem;
ssl_certificate_key /etc/ssl/localcerts/intrexx.example.org.key;
#ssl_password_file /etc/ssl/localcerts/intrexx.example.org.password;
ssl_dhparam /etc/ssl/localcerts/ffdhe2048.pem;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 30m;
ssl_session_tickets on;
# Enable or disable OCSP Stapling
#
# TODO: Enable it (optionally)
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_stapling
# http://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_stapling_verify
# http://nginx.org/en/docs/http/ngx_http_core_module.html#resolver
#
#ssl_stapling on;
#ssl_stapling_verify on;
#resolver 9.9.9.9 8.8.8.8 valid=300s;
# Configure the TLS protocols
#
# TODO: Choose one of modern or intermediate compatibility below.
#
# Modern compatibility (TLSv1.3 only)
#
# TODO: For modern compatibility uncomment the line below.
#
#ssl_protocols TLSv1.3;
# Intermediate compatibility
#
# TODO: For modern compatibility comment out the three lines below.
#
ssl_protocols TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers 'TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384';
add_header Strict-Transport-Security max-age=63072000; # two years
add_header X-Frame-Options SAMEORIGIN;
# hide hidden files and directories
location ~ /\. {
return 404;
}
# hide WEB-INF
location /WEB-INF/ {
deny all;
return 404;
}
# hide IIS web.config
location ~* /web.config {
deny all;
return 404;
}
# hide the bin directory
location /bin/ {
deny all;
return 404;
}
# This is a secret key (security token) that is shared between
# this Nginx configuration and the Intrexx portal. It prevents
# direct connections to the portal's HTTP connector which could
# be a security risk.
#
# TODO: Create the security token as a string only known to this
# configuration and the Intrexx portal (here we use the placeholder
# INSERT_SECURITY_TOKEN_HERE for it). Insert it below.
#
# TODO: Make the corresponding in the portal's web configuration
# file external/htmlroot/WEB-INF/web.xml.
#
# 1.) Set the following property to allow remote connections.
#
# connector.security.header.receiveOnNonLoopbackInterface = true
#
# 2.) Enable the security token by changing the following property.
#
# connector.security.header.secToken.disabled
# -> connector.security.header.secToken.enabled
#
# 3.) Configure the shared security token.
#
# <init-param>
# <param-name>connector.security.token.1</param-name>
# <param-value>INSERT_SECURITY_TOKEN_HERE</param-value>
# </init-param>
#
set $ix_sec_token "INSERT_SECURITY_TOKEN_HERE";
# Delegate WebSocket requests to the Intrexx Portal Service.
#
location /ws/ {
proxy_pass http://backend;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "Upgrade";
proxy_set_header X-SecToken $ix_sec_token;
}
# Delegate requests to the Intrexx Portal Service.
#
location / {
proxy_pass http://backend;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
# Clear potentially unsafe headers. These may be enabled if the backend
# is configured to handle them correctly and in a safe manner.
proxy_set_header Forwarded "";
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Host $host:$server_port;
proxy_set_header X-Original-URL "";
# Security token to authenticate the reverse proxy with the backend.
proxy_set_header X-SecToken $ix_sec_token;
# For security reasons we do not pass X-User and X-Domain to the backend by default,
# since these headers might be interpreted by the External Authentication Filter as
# authenticated user information.
proxy_set_header X-User "";
proxy_set_header X-Domain "";
# additional security sensitive headers
proxy_set_header X-KrbTicket "";
proxy_set_header X-AccountName "";
# Set the maximum allowed size of the client request body. The value 0 disables
# this limit check.
# http://nginx.org/en/docs/http/ngx_http_core_module.html#client_max_body_size
client_max_body_size 2048m;
}
}
Öffnen Sie die Datei mit einem Editor Ihrer Wahl, um die für Sie erforderlichen Anpassungen vorzunehmen.
TODOs
In der Datei finden Sie Anweisungen zur Konfiguration. Diese sind jeweils mit "TODO" gekennzeichnet.
Zentrale TODOs sind:
-
die Angabe des Web Connectors und des Ports
-
Angabe des Servernamens (Full-Qualified-Domainname) und Ports
-
Angaben zu SSL
-
Pfad zur Zertifikatsdatei (*.cer bzw. *.pem) und zum privaten Schlüssel
Wichtig ist zudem die Angabe des korrekte Pfads zum "external/htmlroot" Verzeichnis des Portals.
-
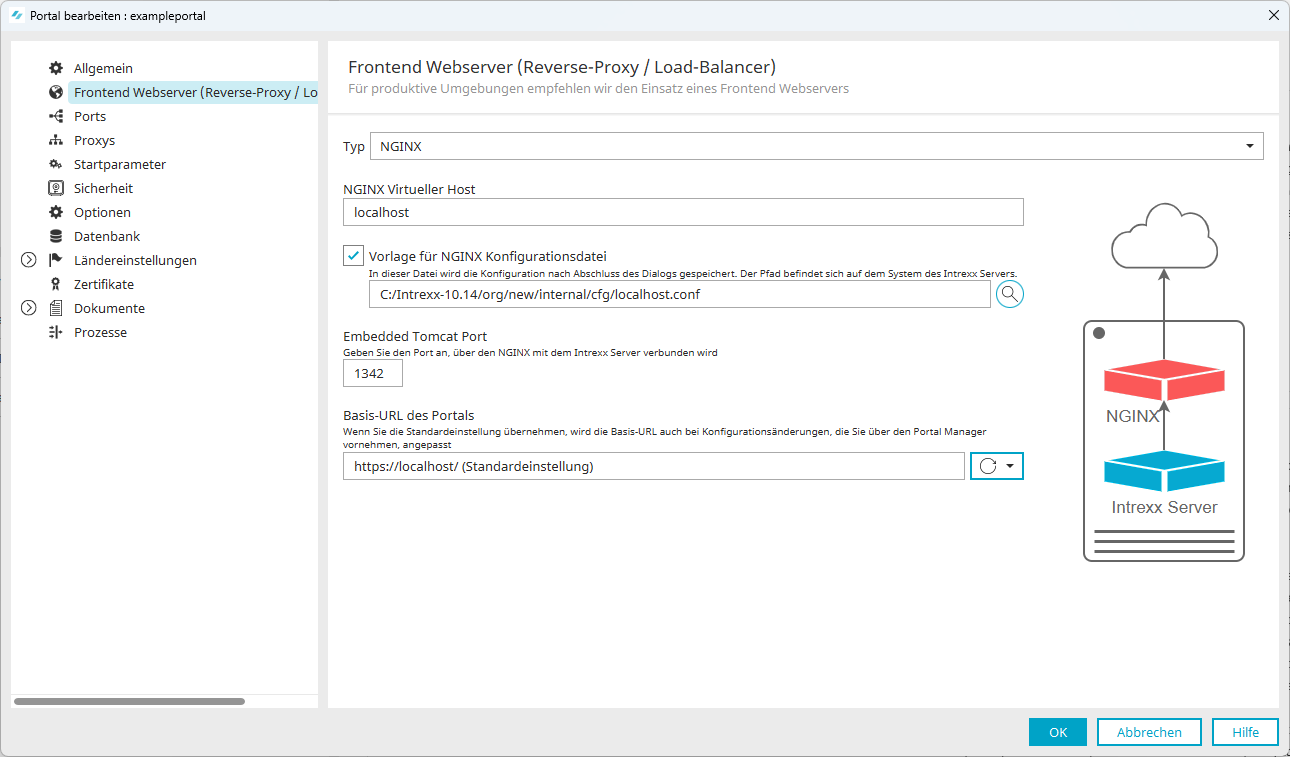
Öffnen Sie hierzu "Portal > Portaleigenschaften > Frontend Webserver (Reverse-Proxy/Load-Balancer) > Frontend-Webserver".
Name
Beschreibung
NGINX Virtueller Host
"NGINX Virtueller Host" bezieht sich auf den Embedded Tomcat. Über den Virtuellen Host nimmt NGINX die Verbindung zum Intrexx-Portaldienst auf. Üblicherweise ist hier "localhost" zu hinterlegen. (Eine Ausnahme kann vorliegen, wenn NGINX auf einem anderen Server als Intrexx installiert ist. In diesem Fall ist dann hier der Intrexx-Server zu hinterlegen.)
NGINX Konfigurationsdatei
Sie können die NGINX-Konfigurationsdatei über Intrexx erzeugen.
Erfassen Sie den Pfad zu dem Verzeichnis, in dem Sie die NGINX-Konfigurationsdatei erzeugen möchten.
Beispiel: /myfolder/portal.example.com.conf
Kopieren Sie anschließend die NGINX-Konfigurationsdatei an die gewünschte Stelle unterhalb von /etc/nginx.
Beispiel: /etc/nginx/sites-available/portal.example.com.confEmbedded Tomcat Port
Hier wird der Port angezeigt, den Sie in der Vorgängerversion von Intrexx verwendet hatten. Diesen Port können Sie belassen.
Hinweis Bei einer Neuinstallation ist hier der Port 1337 voreingestellt.Basis-URL des Portals
Hier muss die Basis-URL hinterlegt sein.
Der erste Teil besteht aus der Angabe des Protokolls. Beachten Sie, dass hier https angegeben ist. Der zweite Teil besteht aus der Angabe des Hostnamens, den Sie in der NGINX-Konfigurationsdatei hinterlegt haben. Beachten Sie, dass ein abschließender Slash (/) angegeben ist. Die korrekte Angabe ist zwingend erforderlich, damit Ihr Portal im Browser aufgerufen werden kann. -
Klicken Sie auf "OK".
Intrexx erzeugt die Konfigurationsdatei. Dabei werden die in den Eingabefeldern erfassten Angaben in die Konfigurationsdatei geschrieben. Die Datei wird im angegebenen Verzeichnis abgelegt.
2. Konfigurationsdatei in Verzeichnis "sites-available" ablegen
Legen Sie die Konfigurationsdatei im Verzeichnis "sites-available" ab.
Hinweis Je nach Linux-Distribution und dem gewählten Installationspaket kann das Verzeichnis "sites-available" gegebenenfalls nicht zur Verfügung stehen.
In der Regel liegen die Verzeichnisse "sites-available/site-enabled" vor, wenn man Nginx aus Repositorys von Debian-basierten Distributionen installiert. Wenn man Nginx aus dem Repository von Nginx bezieht, gibt es die Verzeichnisse nicht. In diesem Fall liegt nur conf.d/ vor. Gleiches gilt für andere Linux-Distrubutionen wie beispielsweise CentOS. Auch hier liegt conf.d/ vor.
Informieren Sie sich in diesem Fall, wie die Konfigurationsdatei bei Ihrer Linux-Distribution implementiert werden muss.
3. Symlink zur Konfigurationsdatei erstellen
Erstellen Sie von sites-enabled einen Symlink auf die sites-available-Datei. Verwenden Sie dabei die vollständigen Pfade.
Hinweis Beim Einsatz von Symlinks sollten Sie darauf achten, diesen direkt im gewünschten Verzeichnis zu erstellen.
Beispiel: "ln -s /etc/nginx/sites-available/host.example.org.conf"
4. NGINX neu starten
Starten Sie NGINX neu.
NGINX und Intrexx auf verschiedenen Servern (NGINX auf Remote-Maschine)
-
Falls der NGINX auf einem anderen Server als Intrexx ausgeführt wird, müssen Sie folgende Blöcke in der Konfigurationsdatei auskommentieren:
Root Direktive (The root path of the Intrexx web application.)
-
Einstellungen für favicon und robots (serve favicon and robots.txt)
-
Einstellung für statische Dateien (Static files that should be served by Nginx)
Das Auskommentieren dieser Blöcke ist erforderlich, damit die statischen Dateien nicht von NGINX ausgeliefert werden, da dieser auf den entfernten htmlroot des Portals keinen Zugriff hat.
-
-
Sie müssen in der Datei "web.xml" (<Portalverteichnis>\external\htmlroot\WEB-INF\web.xml) den "NonLoopback"-Parameter auf "true " setzen.
<init-param> <description> Allow receiving security-sensitive headers on non-loopback network interfaces. Values: true or false (default). </description> <param-name> connector.security.header.receiveOnNonLoopbackInterface </param-name> <param-value> true </param-value> </init-param>
Vergleichen Sie zu diesem Thema auch die Beispiel-Konfigurationsdatei portal-remote.conf.
WebSockets konfigurieren
Damit Sie WebSockets im Zusammenspiel mit NGINX einsetzen können, müssen Sie in der NGINX-Konfigurationsdatei angeben, welche URLs per WebSocket-Protokoll an das Backend weitergeleitet werden sollen. In der Standardkonfiguration stellt sich dies so dar:
...
# Delegate WebSocket requests to the Intrexx Portal Service.
#
location /ws/ {
proxy_pass https://backend;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "Upgrade";
}
# Delegate requests to the Intrexx Portal Service.
#
location / {
proxy_pass https://backend;
...
Hinweis Bei einem Upgrade von einer früheren Intrexx-Version muss die bestehende Konfigurationsdatei entsprechend angepasst werden, damit WebSockets genutzt werden können.
Weitere Informationen zu WebSockets finden Sie in Kapitel WebSockets.