API permissions for the Connector for Microsoft 365 and Teams
You must set the following API permissions in Microsoft Azure to use the Connector for Microsoft 365 and Teams.
Permission types
The types permissions are "Delegated" and "Application". The actions associated with the permissions of the "Delegated" type are performed by a (personal) Microsoft 365 user. The actions associated with the permissions of the "Application" type are performed by a Microsoft 365 service account.
There is often the same permission available for both the "Delegated" and "Application" types. Depending on the use case, you may want an action to be performed by a personal user or by a service account. Therefore, you can select in Intrexx whether Intrexx should log in to Microsoft 365 via a (personal) user or via a service account.
More detailed information is available in section New registration - static user accounts and section New registration - service accounts .
Note that for "Application" permissions, an Entra ID (formerly Azure AD) administrator must give administrator approval.
API permissions
In the input field below, you can enter a term by which the table will then be filtered.
|
API/Permission name |
TYPE |
Description |
Admin consent |
|---|---|---|---|
| Calendars.Read | Delegated | Read access to user calendars | No |
| Calendars.Read.Shared | Delegated | Read users and shared calendars | No |
| Calendars.ReadWrite | Delegated | Has full access to user calendars. | No |
| Calendars.ReadWrite | Application | Read and write calendars in all mailboxes | Yes |
| Channel.Create | Delegated | Create channels | Yes |
| Channel.ReadBasic.All | Delegated | Read the names and descriptions of channels | No |
| Channel.ReadBasic.All | Application | Read the names and descriptions of all channels | Yes |
| ChannelMessage.Read.All | Delegated | Read user channel messages | Yes |
| ChannelMessage.Send | Delegated | Send channel messages | No |
| Chat.Create | Delegated | Create chats | No |
| Chat.Read | Delegated | Read user chat messages | No |
| Chat.Read.All | Application | Read all chat messages | Yes |
| Chat.ReadBasic | Delegated | Read names and members of user chat threads | No |
| Chat.ReadWrite | Delegated | Read and write user chat messages | No |
| Directory.Read.All | Application | Read directory data | Yes |
| Delegated | Show user email address | No | |
| Files.ReadWrite.All | Delegated | Full access to all files that the user can access | No |
| Group.Create | Application | Create groups | Yes |
| Group.ReadWrite.All | Application | Read and write all groups | Yes |
| GroupMember.Read.All | Application | Read all group memberships | Yes |
| GroupMember.ReadWrite.All | Application | Read and write all group memberships | Yes |
| Mail.ReadWrite * | Delegated | Read and write access to user emails | No |
| Mail.Send * | Delegated | Send emails under a different user name | No |
|
offline_access (OpenID Permissions) |
Delegated | Keep access to data for which you have given access | No |
| Presence.Read | Delegated | Read user's presence information | No |
| Presence.ReadWrite.All * | Application | Read and write presence information for all users | Yes |
| Profile | Delegated | Show basic profile of users | No |
| Sites.Read.All | Delegated | Read elements in all site collections | No |
| Sites.Read.All | Application | Read items in all site collections | Yes |
| Sites.ReadWrite.All * | Delegated | Edit or delete elements in all site collections | No |
| Team.Create | Delegated | Create teams | No |
| Team.Create | Application | Create teams | Yes |
| Team.ReadBasic.All | Delegated | Read the names and descriptions of teams | No |
| Team.ReadBasic.All | Application | Get a list of all teams | Yes |
| TeamMember.ReadWrite.All | Delegated | Add and remove members from teams | Yes |
| User.Read.All | Application | Read all users' full profiles | Yes |
*optional
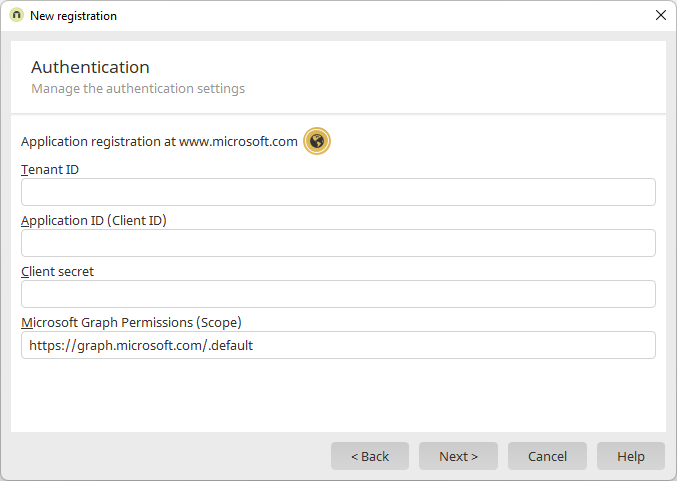
Specify API permissions in Intrexx
In the Connector for Microsoft 365 and Teams "Authentication" menu item you must enter the permissions (scope) with which Intrexx users or Intrexx service accounts are to access Microsoft 365. You can store the permissions individually there. The individual permissions must be separated by a space.
You can also store in Connector for Microsoft 365 and Teams "https://graph.microsoft.com/.default". Intrexx users or Intrexx service accounts then access Microsoft 365 with the permissions you have granted in Microsoft Azure.
More detailed information is available in section New registration - Authentication .